Even if the government and organization are taking initiative to ensure cyber security, the cyber criminals are finding new tactics to break the security wall and find a way in. Cyber-crimes can be seen as a growing plague in today’s society. People nowadays are depending more on internet to fulfil their day to day needs. We can’t even imagine a world without internet. The threat actors are misusing this advantage to make their profit and fulfil their needs.
Recently, an established Canadian aircraft manufacturer, Bombardier was hit by a cyber-breach caused by the supply chain attacks.
The breach was reported on February 23, 2021 where the attacker gained unauthorized access. The hackers have grown too far from confiscating common people to targeting renowned organizations. Immense knowledge about hacking and the use of sophisticated tools help these cyber criminals to take down reputed organizations. At times the amount of data abducted by these criminals makes some companies financially down for years and they take a long time to recover from them.
But the breach in Bombardia was found to have exploited limited amount of data. According to the investigation details, the attacker gained access to a third-party tool by exploiting its vulnerability. This tool was working based on purpose-built servers which were separated from the main Bombardier It network. Vulnerability is the major key hole through which the hackers get in. Checking the vulnerability criteria on a regular basis may help you to defend against most of the cyber-attacks.
The company addresses that as per their security staffs, they have found some of their sensitive data with the ransomware gang Clop’s dark web portal. But as the official investigation progressed, the security experts came to know that the attack was a part of the supply chain breach.
Bombardier reacted abruptly to this incident. They immediately formed a quick response team for investigating the data security breach within the organization. They started to confirm the genuinity of the sources which were connected to them during the time of the attack. Every external client were checked thoroughly and ensured that their security controls were effective.
Bombardier handed over their findings to the official investigation team including the law enforcement and expressed their willingness to corporate with the higher authorities in the inspection process.
The higher officials briefed about the initial findings that the hackers targeted a specific server inside the organization. Other databases like manufacturing process and customer support were untouched. The main aim of the attacker was to abduct sensitive information of the customer and suppliers which was successfully compromised. The inquest pointed that this wasn’t a specific attack which targeted Bombardia, rather a cluster of attacks that spread across the country, out of which one wave hit on this organization.
Trevor Morgan, product manager with the data security specialist presumed that its high time organizations learned from every cyber-attack. We are at a point where the software should always be updated or replaced or replaced it with latest version.
He added that this is a good time opportunity to review the overall working of the organization, cyber security and to check the entry points of every system rooted to the global network.
Bombardier came to know that even small carelessness can bring about hazardous happenings. They must incorporate security alarms if any loopholes or vulnerability is detected. Unfortunately, the major blueprints of the aircraft designed by Bombardia were now available in dark web for free.
The vulnerable FTA web servers were removed from companies as they were found to be hacked in more than 100 companies.
This attack can be seen as a part of unfortunate trend. Since manufacturing technology gained second place in 2020 from the eighth position in 2019, this sector became more feasible and financially stable. So, nowadays attackers are targeting more on modern manufacturing fields.
Supply chain attacks
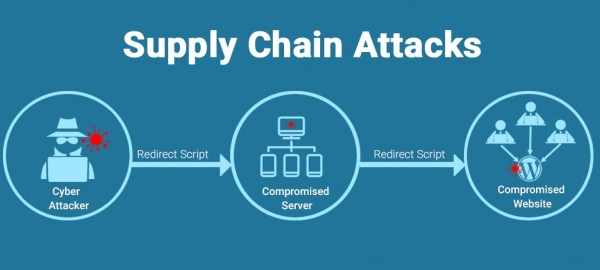
Supply chain attacks happen when someone attacks your system or network by using an outside partner or supplier that has access to your system. These are also known as value chain or third party attacks. Supply chain attacks are trending these days as they are easier to initiate. They do need a direct connection with the main organization, instead they hack the third party agencies with less security protocol and is some way connected to the main stream. By this way they can get inside the target’s network and cause data breach.
Force-stop supply chain attacks
- Ensure who has access to your sensitive information.
- Find the datas which are vulnerable to attacks.
- Ensure the genuinity of the third-party clients and conduct risk assessments.
- Apply access controls.
- Establish Shadow IT.
- Understand and mitigate the malicious insiders.
- Incorporate proper anti-virus detection software.
