Facebook has evolved dramatically. It took a steep rise from being a ‘connectivity’ app to a business-supporting app that runs millions of successful businesses. As you have a wide range of audience, Facebook is an optimum platform to run your business. There are many examples of established businesses that flourished by just using Facebook. Apart from all the positives, there is one main negative which makes people give a second thought about choosing Facebook for business; Facebook hack, and identity thieves.
Today, Facebook offers a wide variety of opportunities and free resources for beginners to initiate their business. Before starting your business, first, you need to create a profile for your business. You must work hard to establish your business account. It is through this business account you will lead your business. After creating the account, just study the Facebook rules for business so that you can protect your business from Facebook hack and other cyber threats. There are third-party applications that help you with this. Try uploading content and blogs daily so that the users will get an idea about your business and create interest in your company.
After updating your company details, link your Facebook URL to your email signature and website. This will help you to brand your business. With the ‘Friend finding tool,’ you can easily find friends you are already connected with. Apart from your business page, create a separate Facebook group or Fan page.
In addition to all this, you must implement relevant Facebook safety measures to protect from Facebook hack. As you cannot control or inspect all the users accessing your page, it is essential to implement necessary security measures.
Make sure you select the right privacy policy
Activate the privacy policy and check for it at regular intervals. Facebook makes changes in the privacy policy, so pay attention to checking and modifying the privacy settings. This helps you to provide a higher level of security to your profile.
Identify and prevent Facebook hack activities
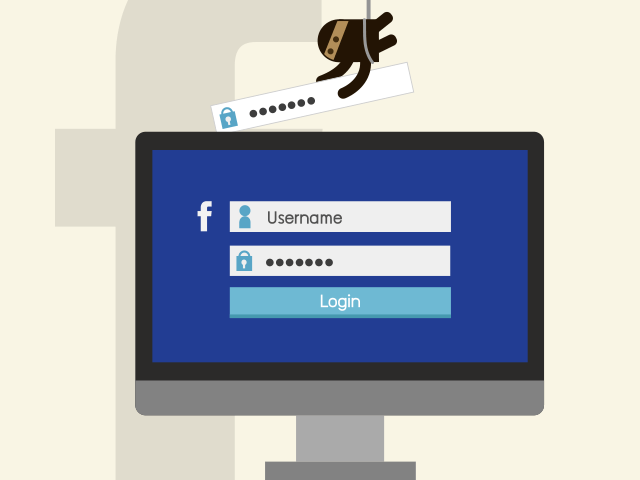
Increasing Facebook business has attracted Facebook hack and fraudsters. They launch phishing scams, fake pages, and rogue applications to trick innocent users. Facebook hackers have set traps in every nuke and corner of Facebook such that you may end up linking your business page with malicious networks and pages. A strict analysis will help you prevent Facebook hack activities and establish an effective privacy and security policy.

Always scan and decode external links
When you are dealing with a business profile, you may have to allow other users to post external links, images, and other content on your wall. You cannot predict the intention of the people accessing your business page. So it is always safe to run a regular scan and decode links posted on your wall.
Secure important information and data to defend Facebook hack
While running a business, you will have to post information about your business on Facebook. Only then customers will know about your business and it will grow. Your business page will be an efficient medium to communicate and interact with existing and prospective customers. Since you are dealing with sensitive information, it is important to protect your business data and information.
Keep it personal
While dealing with a business account, you must be careful. When someone becomes your follower, you should welcome them. But, make sure that you activate your privacy settings. Also, you will receive a lot of comments on your post which will also contain links. Make sure that you don’t open those links because they may be infected and set by Facebook hackers to hack your account.