Today’s organizations are successful in incorporating the Internet of Thing (IoT) into their business techniques after realizing the huge benefits from their processes, employees and customers.
As IoT has marked its steep growth in the business sectors, it’s challenging the network and the security teams alike. Conventional network defences does not make an effective technique to defend the attack against IoT devices.
Beyond that, the IoT security solutions fail to address the entire challenges faced by IoT devices.
Today, about 30% of IoT devices are connected to the end points of every network in an organization. It’s high time for the CISOs and the security leaders to think about a complete IoT “lifecycle approach” to ensure IoT security and enables their protection
from new and unknown threats. The lifecycle approach enhances the five critical stages of IoT security.
IoT is one of the most sophisticated and versatile technologies existing today. The omnipresence of internet, growing network connections and diversity of connected devices makes IoT systems more adaptable
IoT has brought about revolutionary changes in manufacturing, finance, food production, healthcare and energy specifically through the extension of its own kind, Industrial Internet of Things (IIoT).
It has also helped in the development of smart homes, buildings and cities.
Every growth has its consequences.
How can IoT influence security?
Certain characteristics of the IoT systems and devices causes risk to the underlying technological process. This characteristic makes IoT environmentally functional and efficient, but they are prone to threat actors.
Some of the major characteristics include:
- Gathering abundant data: IoT devices gather detailed information from the users and environment. This data is a major criterion for the IoT systems to function efficiently. However, this data could pose a severe threat if not secured properly stolen or comprised.
- Connection of virtual and physical environment: IoT devices are proficient to function using the data they receive from the respective environments. These abilities cut shorts the distance between virtual and physical systems. Apart from user’s convenience, it allows the cyber hacks to translate physical consequences very quickly thereby creating a greater impact.
- Creation of complex environments: Growing diversities in devices has created complex IoT environments. The word “complex” implicates that more than one IoT devices can work using a single IoT environment that has dynamic interactions between devices. This complexity can sometime cost a wider attack surface.
- Centralization of architecture: Applying a centralized architecture pattern to the IoT devices can have detrimental effect on security. The patterns include gathering all the data or each device and communicating it to the base station. In an organization the main data base could be a source to thousands of other devices that gathers an astonishing amount of data. This is less costly and efficient than having a separate database. But when it comes to attack, it is intricately connected to a single root.
Attacking platforms of IoT
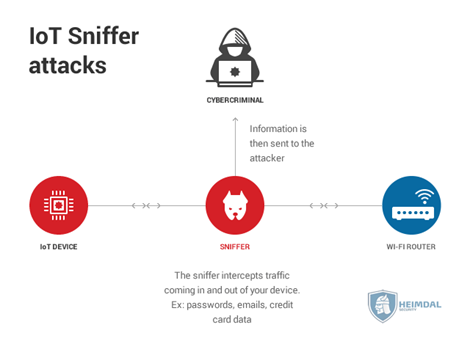
As a part of the IoT project, the Open Web Application Security Project (OWASP) has published a detailed list of attacking platforms and areas where vulnerabilities may possibly exist.
- Devices: Devices are the primary platforms where the cyber-attacks are initiated. The main areas of vulnerabilities include memory, firmware, web interface, physical interface and network services. The hackers can also take advantages of unsecure mechanisms and out-dated components.
- Communication channels: Channels connected to IoT devices are also prone to cyber hacks. The protocols that are used in IoT systems may have security issues that can infect the entire systems. IoT systems are mainly attacked by using Denial of Service (DoS) and spoofing techniques.
- Applications & softwares: Vulnerabilities or patches in the software may lead to cyber-attacks. Web applications are mainly hacked to steal user credentials and push malicious firmware updates.
How to secure your IoT devices?
- There must be a proper record of all the gathered information
Every data and information communicated within the IoT devices should be monitored and recorded. The information also consists of credentials in the automated servers and other IoT applications.
- Every devices connected to the IoT should be configured
Security of the systems should be ensured before connecting to the IoT platform. Incorporate a strong username and password combination, multi-factor authentication and encryption.
- The security strategy should be built without any compromise
To avoid breach and compromising of data, it is more important to acknowledge that there is no proper defence mechanism for the evolving threat that can help in creating mitigation protocols which reduces the effects of successful attacks.
- Each device should be secured physically
Physical accessibility of IoT platforms is a major factor to be considered while creating a security protocol. IoT devices should be protected from physical tampering. If not taken care, attackers may implant malicious hardwares or softwares to spread malware.
