Emotet, the most dangerous malware existing was taken down by the police department making the people around the world free from million dollar data thefts and thereby reducing the maintenance fee for the computer, software and network.
In the widespread search for Emotet, countries like UK, US, Canada, Ukraine, Holland, France and Germany participated in the mission.
The Emotet was first found in Europe in 2014 after which it expanded and became the cause for millions of cyber-attack across the globe.
The first FBI case of Emotet was registered in 2017 when a North Caroline district school data was compromised.
Jessica Nyc, a cyber-crime supervisor at FBI claims that Emotet had substantially evolved from its first variant. The stealth value of the malware went high and opened a new door for additional malwares.
As per an article in BBC, this malware had sent over 150,000 phishing emails with 100,000 different subject lines.
The FBI describes Emotet as “nimble” and ever mutating malware. Once the target checked the ‘enable macros’ in the word document, it opens a backdoor into the devices and the hackers would send Trojans through them that would record the banking information of the target.
As per the reports of Europol, cyber police had took control of Emotet’s inside infrastructure which inversely means to put a lock to half of the devices spreading malware and has separated them server by server.
According to Nyc the combined efforts of FBI team, foreign partners and private sector partners significantly helped to control the network of Emotet.
How this spreads?
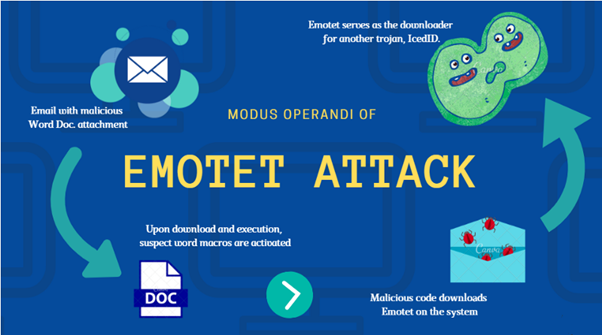
Emotet spreads through word documents. As studies suggest Emotet malware is delivered to victims through infected mail attachments. Wide variety of techniques was used to make the target open the malicious attachment. Some attachments can come in the form of shipping notices, invoices or even information about COVID-19.
The attachments mainly consisted of word documents. Once a user opens this document, they are induced to “enable macros” function such that the infected code runs in the device and installs Emotet in the target device.
Hiring malware
The job of Emotet was more than that of a malware. Why is Emotet called the most dangerous malware is that they were offered to hire for other cyber hackers to install other types of malwares such as infectious Trojans.
This type of attack is generally known as “loader” operation and other malwares operators like Ryuk & Trickbot has benefitted from them.
The infrastructure
Emotet is controlled by several hundred servers located across the globe, each of one having different functionalities to manage the infected computers, to spread new malwares and to serve criminal groups.
To break the Emotet infrastructure, the government agencies has teamed up to create a new strategy. This helped the FBI and the government to take down Emotet from inside. The infected systems have been redirected towards the law enforcement controlled infrastructure. This was indeed a unique and a new approach.
Defend Emotet
Emotet unlike other botnets are polymorphic in nature. That is its code keep on changing when it is called up. Since most of the anti-virus scans for known malware codes, Emotet is difficult to discover due to its code changing feature.
So, in order to detect the malware, we need a combination of anti-virus with the operating system that together creates a cyber-security tool.
Users should be very cautious while checking the email and should avoid opening attachments from unknown senders.
A Dutch National Police conducted a detailed investigation about Emotet and found that a database containing email addresses, passwords and username were stolen by Emotet.
The Computer Emergency Response Team has created a network through which the notifications of affected people were available, as a part of global remediation strategy.
