We all use social media. The level of usage depends on one person to another. But still an average person spends a minimum of 2 hours per day in social networking sites. We feel happy connecting to our family and friends who are far away. Social media platforms are improving their features in every updates and now the developers has included features that can be used to showcase talents, for example reels in Instagram. When Tik Tok was banned in India, reels came into being. We can see a lot of talented people performing their talents which are viewed by millions of people. So in a way social media is a method to remove boredom and gives pleasure.
Apart from these positive sides, social media has equally a negative side. The major one is the health and the mental issue caused due to them. Cyber-attacks in social media are gaining popularity and are increasing day by day. The hackers make use of the vulnerabilities in the social media to exploit the users. Hackers develop tools and strategies based on these vulnerabilities. After every attack, they think about a new technique that can improve the way hacking is carried out.
When it comes to Instagram attacks, hackers mainly concentrate on stealing high profile accounts as they will have a greater fan base. Recently, a group of Turkish hackers were found to hack the profiles of well-known people by sending phishing messages through Instagram chat which looked legitimate.
Main targets of such groups include celebrities, politicians, social workers, business owners and other well treated people in the society with a reasonably good amount of followers.
Apart from entertainment, Instagram plays a major role in marketing various products and services. Businessmen get majority of profit in their business from these advertisements. If the ads are through verified profiles then the business is tend to have a steep growth. These kinds of profiles are the favourites for the hackers. They use these accounts for various purposes like blackmailing, spreading scams or to show off their hacking skills.
Similar approach, different techniques
The main motive behind an Instagram hack is to take control of an account and use it for various causes as mentioned above.
The threat actors often develop phishing links which calls the target to confirm their account settings and to verify the user. The page looks so legitimate that it was looks like the confirmation message from the original web developer. Once, when the target clicks “verify account” he is redirected to a phishing page which makes you to compromise personal information like email ID, password, DOB, credit card details etc.
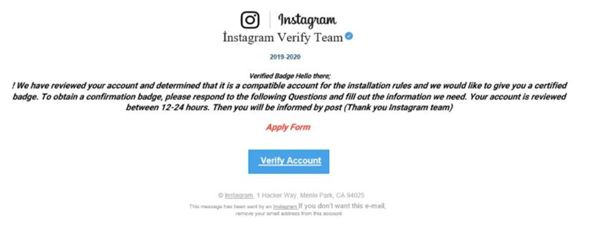
From this old tactic, cyber hackers have exploited to a fresher method. Here the threat actor will send the phishing link through Instagram direct message. They will claim that your account is in danger due to copyright issues and there is an urgent need to confirm the user of the account, if not the account will be deleted as per cyber act rules. The message ends by providing a link to verify yourself.
People usually fall for this scam believing that these notifications are from trusted sources. Once the link is opened, it redirects you to another tab that asks you to provide your username.
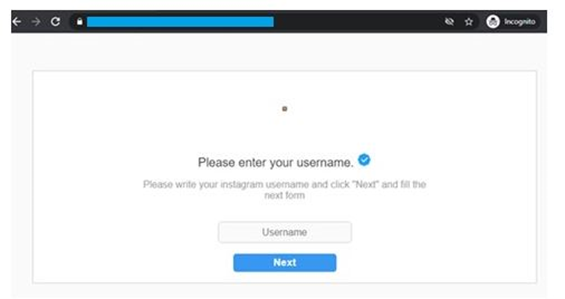
When you enter the username and click on the “next button”, another tab opens. This time it seeks for more personal information like name, password, email and email password.
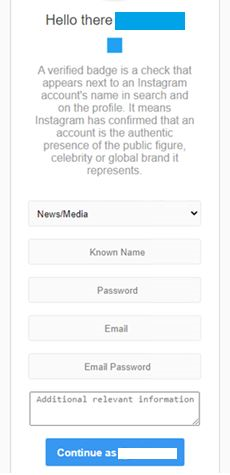
When everything is entered, the page redirects you to the login page of Instagram. If you have already logged in, it will redirect you to the homepage saying that all the details you have provided will be connected to Instagram.
So as you have entered all your login credentials, the hacker will now use the credentials to unlink yourself from your Instagram account. He will unlink your email and phone number linked with the account. Now he will have the complete control over your account.
He played the queen’s gambit move and you fell for it. Checkmate!
Look out for scams, protect your account
- Check and be cautious about legitimate looking websites that asks for your login credentials. It can be a phishing a attack.
- Always enable the 2 factor authentication feature. This gives an extra layer of security to your account.
- Never open attachments or links from strangers. Even check the URL of websites before entering.
- Check the content of the web page. Examine the construction of sentences and look out for grammatical error.
- Avoid mails or messages that requests for your personal information.
