What is spoofing?
Spoofing is a fraudulent act in which communication from an unknown source is disguised as being from a source that is known to and trusted by the recipient. A spoofing attack occurs when a person (referred to as a spoofer) pretends to be someone else in order to trick their target into sharing their personal data or performing some action on behalf of the spoofer. The spoofer will often take time and make an effort to build trust with their target, thus ensuring that they will share their sensitive data more easily.
Let’s now look on to content spoofing
Content spoofing, also referred to as content injection, “arbitrary text injection” or virtual defacement, is an attack targeting a user made possible by injection vulnerability in a web application. When an application does not properly handle user-supplied data, an attacker can supply content to a web application, typically via a parameter value, that is reflected back to the user. This presents the user with a modified page under the context of the trusted domain. This attack is typically used as, or in conjunction with, social engineering because the attack is exploiting a code-based vulnerability and a user’s trust. As a side note, this attack is widely misunderstood as a kind of bug that brings no impact.
This technique is also referred to as content injection or virtual defacement, according to the OWASP group. This attack is generally used as, or in conjunction with, social engineering (e.g., via e-mail or any social networking sites). This attack is developed by exploiting a code-based vulnerability and the user’s trust. In some cases, an attacker may modify information and links in an established website by alerting content on the server. The later one is more difficult to detect by a user, since there is no readily apparent difference to the casual observer.
Types
There are two basic kinds of injection possible here:
- Text Injection
- HTML Injection
Text Injection:
Text Injection is a subcategory in which the user will be able to inject only plain text into the page. In other words, it is not possible to inject executable JavaScript content, shell commands or HTML content. The user in majority of the cases might just be able to change some of the text content that is already on the website.
HTML Injection:
HTML injection is similar to text injection and as the name suggests it allows HTML content to be injected. This is a relatively severe class of Content spoofing vulnerability as it is possible to make offensive content more visible with HTML more than using plain text.
When a web application does not properly handle the data that is supplied by the user, an attacker can supply the content to the web application by modifying a parameter value, which in return is reflected back to the user of the web application.
The most dangerous form of content spoofing is done with DHTML (dynamic HTML) content sources such as fill-in forms and login forms. When a web-page with spoofed content is viewed by an internet user, the URL bar displays a legitimate URL, although it isn’t. As a result, when the user of the website enters sensitive information such as username, password, birth date, credit card details, or SSN (Social Security Number), the attacker can obtain this victim’s data for identity theft or other malicious purposes.
Safety Measures
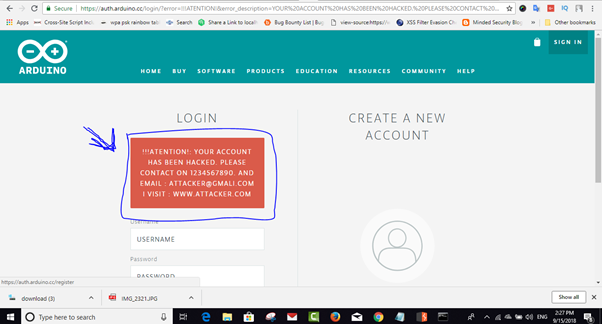
- Never Construct and send Error messages via request parameters.
- Prefer Using Messages predefined in a property file.
- Avoid passing HTML content via from request parameters.
- In case of a need to pass any HTML content do encoding/filtering before rendering as HTML
- Pass Internal message keys to get predefined message values or some unique ids to identify the content to be displayed